In order for systems to work in networks, some ports must remain open for necessary unprotected communication, such as DHCP or DNS.
Your administrator will determine which ports will remain open for what kinds of unprotected communication. There are some common security exceptions that your administrator might want to incorporate in the network.
Important Note:
Security exceptions, by definition, mean that your system is vulnerable to attacks from intruders on the ports that are defined on your system. Use caution in defining ports on a system that will Allow Communication without Security. These unprotected ports pose a security risk.
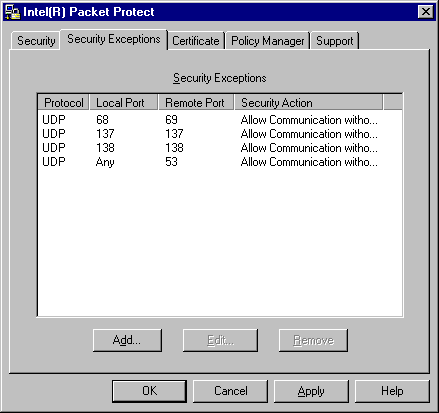
Security exceptions display on the Security Exceptions tab:

A security exception contains these elements:
| Protocol | Security exceptions can use either a UDP or TCP
protocol. UDP (User Datagram Protocol) is a connectionless IP (Internet Protocol) protocol. UDP offers few error recovery services. Instead, it offers a direct way to send and receive datagrams over an IP network. UDP is primarily used for broadcasting messages over a network. TCP (Transmission Control Protocol) is a connection-oriented IP protocol. TCP ensures that packets are received in the same order that they were sent. It also implements flow control, which ensures that the destination is not bombarded with packets. |
| Local Port | A port number for this computer, normally. It can also be a port number for a broadcast address that also maps to this computer. |
| Remote Port | A port number for the computer that this computer is communicating with. |
| Security Action | Valid choices are Allow Communication without Security and Deny Communication. |
How do I add a security exception?
How do I modify a security exception?
How do I delete a security exception?
Copyright © 2000, Intel Corporation. All rights reserved.
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for explanation and to the owners' benefit, without intent to infringe.