IPSec is a set of standard protocols developed by the Internet Engineering Task Force (IETF). IPSec is used to protect the privacy and integrity of IP communications. It protects IP communications using algorithms that perform encryption and authentication tasks, as well as other features that enforce additional protection.
If IKE successfully negotiates a protected communication, it passes the agreed upon information to the IPSec driver used by Intel Packet Protect. Then, the IPSec driver uses that information to determine how to protect the IP communication.
IP communications use security associations to protect traffic in the LAN. After a security association is set up between two systems, the systems can exchange data and IPSec will protect that data using a collection of the following settings:
Note: Anti-replay protection is built into Intel Packet Protect. In all situations where anti-replay protection makes sense to use, Intel Packet Protect ensures that you have that protection.
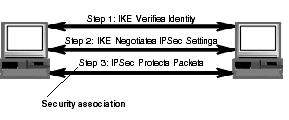
The diagram below shows the steps that Intel Packet Protect performs to protect a communication. The security association is established in Step 3.
Security associations expire if they reach the maximum threshold defined for the communication. Intel Packet Protect is designed to automatically re-negotiate the security association when it is about to expire (usually when it reaches approximately two minutes of its lifetime), whether or not the security association is in use. The renegotiation will only happen if the traffic is generated between the two systems:
Intel Packet Protect re-negotiates the IPSec settings only; it doesn't need to re-verify the identity of the systems because it is already known. This helps reduce network traffic by reducing extra key generation.
If the security association is not renewed automatically and consequently expires, a security association between the same systems will require both IKE steps: identity verification and IPSec negotiation.
IPSec applies the selected algorithms to each packet that is protected by IPSec. The algorithms provide one of the following protection features:
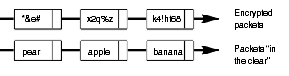
Use encryption to protect the confidentiality of packets. Encryption encodes packets so they are unreadable unless the receiver has the proper key to decode the packets.
If a packet is encrypted using ESP encryption (DES or 3DES algorithms), it is unreadable while in transit. Other types of encryption can protect the confidentiality of information while stored on a system— Intel Packet Protect is designed to protect the confidentiality of information while traveling on the network. The following diagram shows unencrypted and encrypted packets traveling on the network.

If the packets pass through any routers or switches, the encrypted packets are relayed without requiring IPSec on those devices.
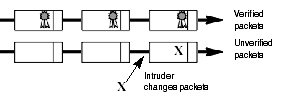
Data integrity verifies that the packet was unchanged during transport over the network. It also verifies that other packets were not inserted into the packet flow. This helps prevent a system from accepting packets from an intruder who is attempting to send packets on the network.
Use integrity features to protect the authenticity of packets, that is, verify that the packet was unchanged during transport over the network. Integrity features also verify that no other packets were inserted into the packet flow.
Intel Packet Protect uses ESP and AH algorithms (MD5 or SHA-1) to protect the integrity of packets.
The following diagram shows two sets of packets traveling on the network. The first set uses integrity protection; the second set, does not.
Copyright © 2000, Intel Corporation. All rights reserved.
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for explanation and to the owners' benefit, without intent to infringe.