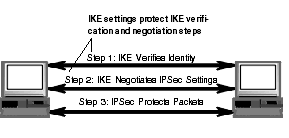
When IKE verifies the identity of two systems, it requires that the IKE settings be compatible.
IKE settings are agreed upon by the two systems that are attempting to verify each other's identity. They are used to protect the IKE negotiation transactions. This allows the two systems to negotiate without compromising secret key or password information.
The diagram below shows the steps that Intel® Packet Protect performs to protect a communication. The IKE settings are used during Steps 1 and 2.

Intel Packet Protect uses pre-defined IKE settings, designed for maximum compatibility with systems that use Intel Packet Protect and other IPSec products.
If two Intel Packet Protect systems attempt to communicate, they use the same default IKE settings. If one of the systems is managed by a different IPSec product, make sure that the IKE settings match. If necessary, make changes to the IKE settings in the other IPSec product. The following table describes the pre-defined IKE settings for each system that uses Intel Packet Protect.
|
Preferred |
Encryption |
Hashing |
Diffie- |
|---|---|---|---|
|
1 |
DES (56-bit) |
MD5 |
768-Bit |
|
2 |
DES (56-bit) |
SHA-1 |
768-Bit |
|
3 |
3DES (168-bit)- not available in DES-only version. |
MD5 |
1024-Bit |
|
4 |
3DES (168-bit) - not available in DES-only version. |
SHA-1 |
1024-Bit |
A system that requests a protected communication proposes its list of IKE settings to the system with which it is trying to communicate. The IKE settings are proposed in order of preference, but the initiating system can agree on any of the proposed combinations. The responding system must have one of the combinations defined, or the communication is not allowed using IPSec.
Note: The IKE settings used by Intel Packet Protect cannot be customized. If you require different settings for a communication with a system that uses a different IPSec product, change the IKE settings in the other product to match one of the IKE setting combinations used by Intel Packet Protect (as noted in the above table).
Copyright © 2000, Intel Corporation. All rights reserved.
Intel Corporation assumes no responsibility for errors or omissions in this document. Nor does Intel make any commitment to update the information contained herein.
* Other product and corporate names may be trademarks of other companies and are used only for explanation and to the owners' benefit, without intent to infringe.